Pwnable.kr - Toddler's Battle - [fd]

Description
This post will focus on an easy pwn challenge fd from pwnable.kr
Starting off we have the following description.
As the name and description suggests, this challenge has something to do with the file descriptors in linux.
Let’s ssh into the machine.
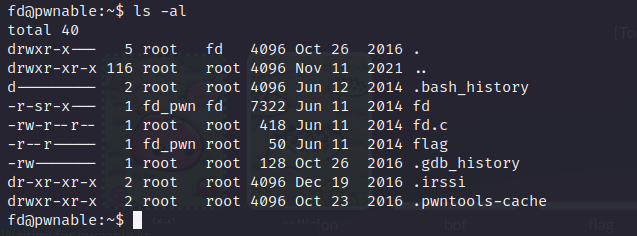
We have the following files.
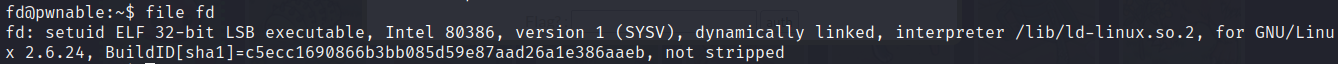
Checking the fd file.
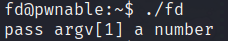
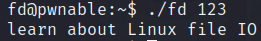
Running the binary.
We have to provide a number as argument but whatever we write for now it returns Learn about Linux file IO
Exploitation
Looking at the source code of the binary.
|
|
In line number 10, an int fd variable is declared which will be used as a file descriptor.
Source: https://stackoverflow.com/a/5256705
The 3 basic values for file descriptors are 0 for Standard Input (stdin), 1 for Standard Output (stdout) and 2 for Standard Error (stderr).
Back to our code, the value of our argument is getting subtracted by a hex value 0x1234.
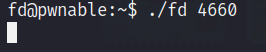
Converting to decimal it becomes, 4660.
Now if we provide 4660 in the argument the value of file descriptor will become 0.
Meaning we can then enter any value to the buffer.
From line 12 to 17, it simply reading standard input and saving it to the buffer. Then it’s comparing the value of the buffer with the string LETMEWIN.
So we simply write LETMEWIN and hit enter to get the flag.
Thanks for reading!